1
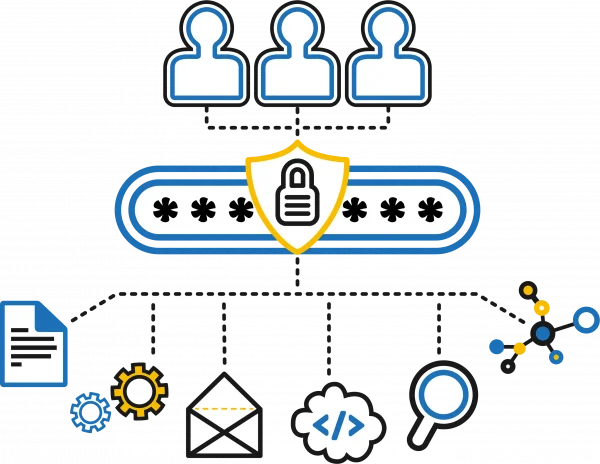
Local Administrative Accounts
Non-personal accounts that grant administrative rights on individual machines or systems.
2
Domain Administrative Accounts
Accounts that offer privileged access across all devices, services, and workstations within a particular domain.